Network Isolation
Sirveo features a network isolation capability, which is useful for improved security.
Sirveo’s HTTP server has two logical components:
- An admin API & UI, which provides system management
- An inbound API & UI, which only provides inbound access to flows (if configured via links and/or webhooks).
The server’s primary HTTP server (default port: 7001) always includes both components. This is referred to as the admin server in the configuration.
Optionally, a second HTTP server (default port: 7005) can be enabled, which only provides HTTP access to the server’s configured webhooks and links. This is referred to as the inbound server in the configuration. It is not possible to access the admin API & UI on the inbound port.
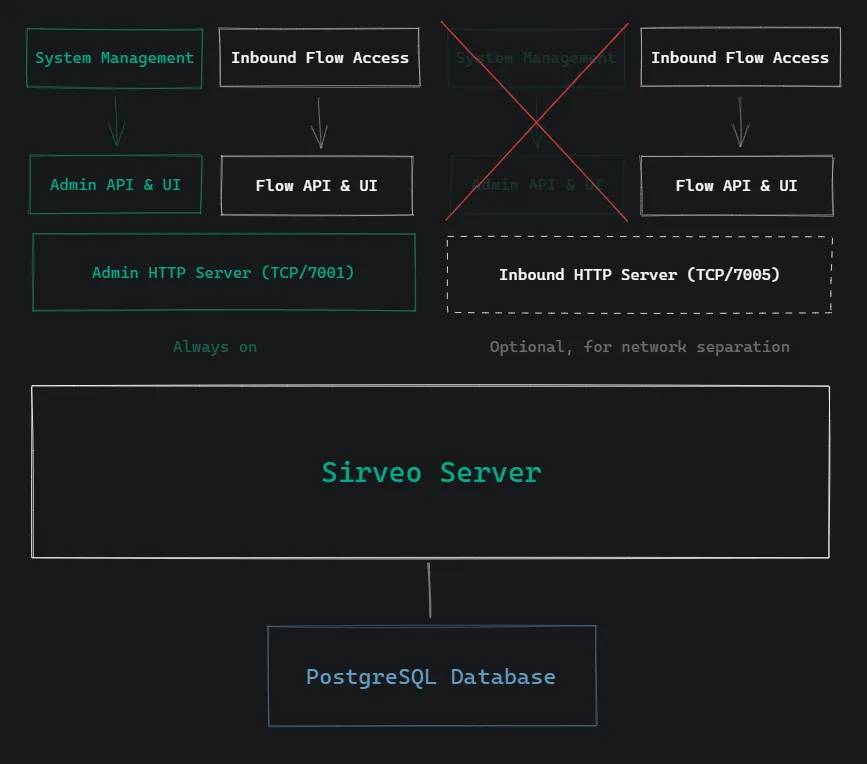
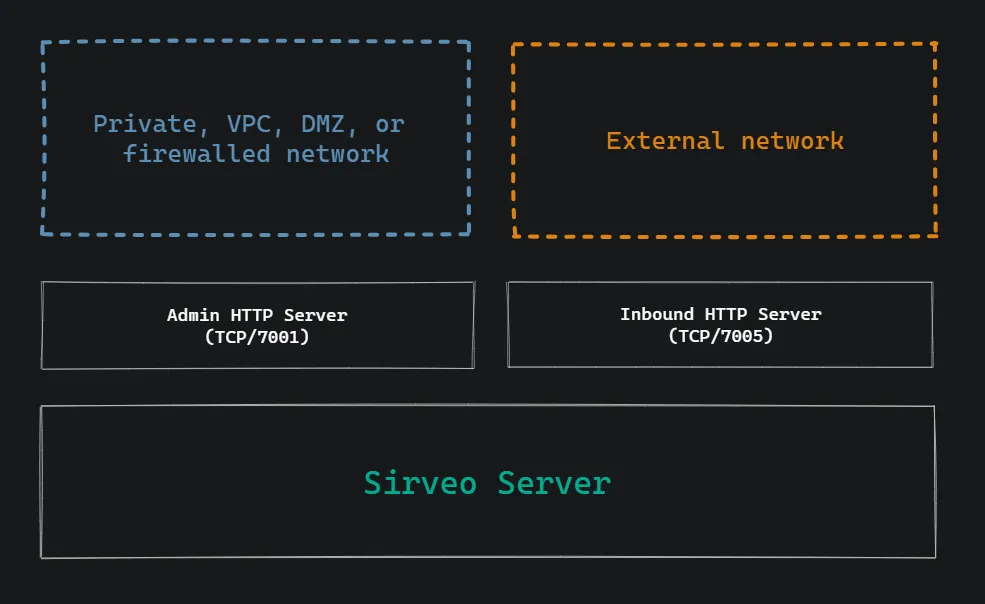
This feature simplifies deployment scenarios where network isolation is desirable. For example, the admin API & UI can be kept within a private network, while the inbound API & UI - with no administrative access - can be exposed in a less-trusted, or untrusted network.
Example Configuration
Suppose you want to configure a Sirveo server with:
- It’s admin API & UI on domain
sirveo.mydomain.io - It’s inbound API & UI on domain
automation.mydomain.io
Let’s assume you are using a web server like Caddy to front Sirveo, for TLS termination and automatic certificate renewal.
First, configure Caddy as a reverse proxy to Sirveo’s admin port.
sirveo.mydomain.io {
reverse_proxy * { to http://localhost:7001 header_up X-Forwarded-For {remote_host} }}Then a similar configuration for the inbound port.
automation.mydomain.io {
reverse_proxy * { to http://localhost:7005 header_up X-Forwarded-For {remote_host} }}Given this setup, configure the Sirveo server’s listen addresses:
# default admin & inbound portslisten_address_admin: localhost:7001listen_address_inbound: localhost:7005For the admin UI to generate correct URLs to webhooks and links on both admin and inbound ports, tell the server how it is being accessed externally:
# external urlsurl_admin: https://sirveo.mydomain.iourl_inbound: https://automation.mydomain.ioLastly, the server does not trust client IP headers by default, because these are easily spoofed. The server should be configured explicitly, according to how the upstream proxy will forward client IP addresses. In this case:
# where to find proxied client IP addressesip_header_admin: X-Forwarded-Forip_header_inbound: X-Forwarded-ForWhen webhooks and links are configured on the server, they will be available on both domains. But the admin API & UI is only available on sirveo.mydomain.io.
In this manner, it is easy to further limit access to the admin port only locally, or on an internal network or VPC.